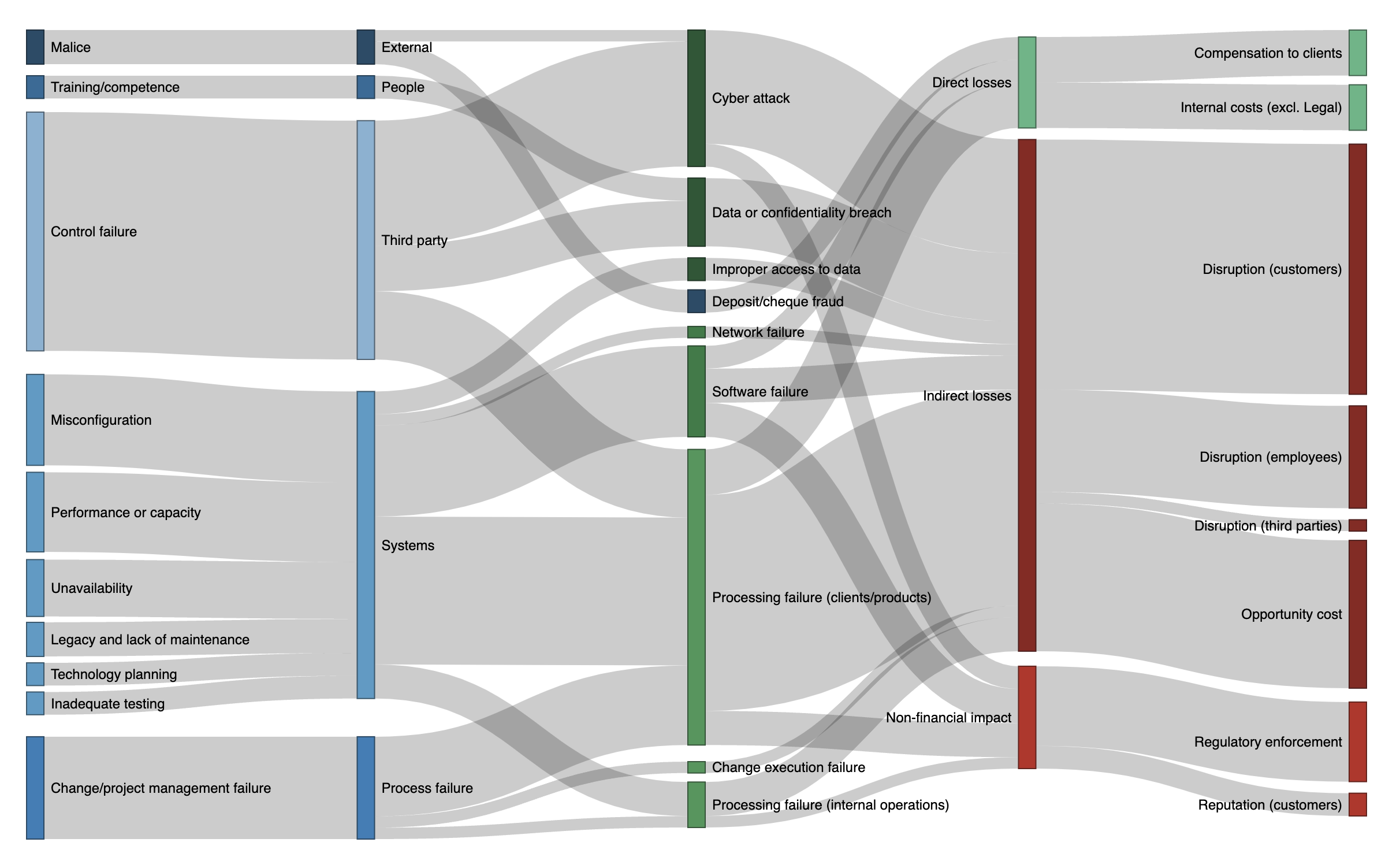
Senior managers talk about risks, and not about threats or controls. To have better conversations with senior leaders, focus where the risks are coming from, and why. This post offers a vocabulary for talking about cyber- and technology-related risks and their causes.


